n8n Hostinger Automation Guide
September 26, 202516 Mins read62 ViewsContentsShare and exportCreate
A Comprehensive Guide to Mastering Workflow Automation: Self-Hosting n8n on Hostinger
Part I: The Strategic Case for Self-Hosted Automation
Chapter 1: The Automation Imperative: Why n8n?
1.1 The Genesis of a New Automation Paradigm: What is n8n?
Workflow automation has evolved from simple trigger-action sequences to complex, multi-step processes that integrate disparate business applications and data sources. At the forefront of this evolution is n8n, an open-source tool designed to handle these intricate demands. Described as a versatile “digital assistant” that connects applications and services, n8n allows for the creation of automated processes without the need for extensive custom code.1 Its core purpose is to streamline repetitive tasks, freeing up human resources for more strategic work.2
The fundamental architecture of n8n is built around a visual, node-based system.2 Each “node” represents a specific step or action in a workflow, such as fetching data from an API, updating a spreadsheet, or sending a notification.2 These nodes are connected in a logical sequence via a drag-and-drop interface, visually mapping out the entire automated process.4 A typical workflow begins with a
Trigger Node, which initiates the process based on an event—such as a new form submission, a webhook, or a scheduled time—and then proceeds through various Action Nodes that define the subsequent logic and tasks.2 This modular approach makes it exceptionally easy to configure and manage complex workflows, enhancing overall efficiency.4
While n8n is celebrated for its no-code visual interface, its true power lies in its hybrid, “low-code” philosophy.4 For users with technical proficiency, the platform provides the flexibility to inject custom JavaScript or Python code directly into a workflow, enabling sophisticated data manipulation, complex algorithms, or custom logic that would be impossible with a purely no-code tool.5 This dual capability makes n8n a uniquely adaptable solution, serving both users who need a simple visual builder and developers who require full control. The open-source nature further enhances this flexibility, as workflows are treated as portable, editable objects that can be versioned, shared as JSON files, and easily re-imported into any environment, promoting collaboration and reusability across an organization.3
1.2 The n8n Advantage: A Detailed Comparison with Zapier and Make.com
When considering an automation platform, the choice often comes down to three major players: Zapier, Make.com, and n8n. Each platform offers a distinct philosophy and value proposition tailored to different user profiles and business requirements.7
- Zapier is renowned for its user-friendliness and massive library of over 8,000 pre-built integrations.6 It operates on an intuitive trigger-action system that can be mastered in a matter of hours, making it the ideal choice for beginners and non-technical teams seeking to integrate standard SaaS applications quickly and with minimal effort.5 However, its focus on simplicity means it offers limited customization and may quickly reach its limits for complex business logic.8
- Make.com (formerly Integromat) provides an excellent middle-ground solution. It features a powerful visual interface and offers deeper, more intricate integration options for each connected service compared to Zapier.8 The platform is well-suited for intermediate users who need to perform sophisticated data transformations and create complex conditional logic without resorting to custom code.8
- n8n, in contrast, is the optimal tool for technical teams and companies that demand deep customization, data ownership, and robust scalability for high-volume processing.5 While it has a more substantial learning curve that can span several weeks, the platform offers an unparalleled level of technical flexibility, including the ability to run custom code and access the file system for complex operations.5 For projects that require strict data privacy compliance, such as GDPR, the self-hosting capability of n8n is a non-negotiable advantage.5
The fundamental difference between these platforms becomes most apparent in their pricing models. Zapier operates on a per-task model, where every single successful action in a workflow counts as a task.6 This means that a multi-step, high-volume workflow can quickly become unpredictably and prohibitively expensive. In contrast, Make uses a
per-operation model, where each module action is an operation, which can offer better cost efficiency for complex scenarios than Zapier.5 However, it is n8n that offers the most cost-effective and predictable solution for high-volume automation.8 The n8n Cloud plan charges a fixed fee
per workflow execution, regardless of the number of steps or tasks within that workflow.6 This is a significant distinction, as it removes the financial penalty for building complex, multi-step automations.
This difference in pricing philosophy creates a powerful long-term strategic advantage for businesses. With Zapier, a business must constantly perform a cost-benefit analysis, potentially sacrificing functionality to avoid escalating expenses. In this model, adding more steps or processing more data directly correlates with higher costs. With self-hosted n8n, this dynamic is fundamentally altered. Since the only cost is the server infrastructure, a business can build the most intricate, data-intensive, and powerful workflows imaginable without incurring additional fees for each individual task. This positions self-hosted n8n not merely as an alternative, but as a superior, long-term platform for scaling businesses and managing high-volume, data-intensive projects, such as those involving AI pipelines.4
| Criteria | n8n | Make.com | Zapier |
| Pricing Model | Free (self-hosted) / Per workflow execution (cloud) | Per operation | Per task |
| Ideal User Profile | Technical teams, developers, users requiring control & privacy | Intermediate users, teams needing robust data transformation | Beginners, non-technical users |
| Learning Curve | Substantial (weeks) | Moderate (days) | Minimal (hours) |
| Self-Hosting | Yes, free Community Edition | No | No |
| Integrations | 1,000+ pre-built, plus custom nodes & any API | ~2,000 with deep integration options | 8,000+ |
| Data Control & Privacy | Complete control on self-hosted instances | Data resides in the cloud | Data resides in the cloud |
| Extensibility | Unlimited via custom JavaScript/Python code and system commands | Excellent customization via visual interface and custom functions | Limited customization, relies on pre-built actions and filters |
Chapter 2: The Hostinger Foundation: A Strategic Choice for n8n
2.1 Why a Virtual Private Server (VPS) is Non-Negotiable
The decision to self-host n8n requires a solid, reliable foundation, and this is where the choice of hosting provider and service type becomes critical. While shared web hosting may seem like a cost-effective option, it is entirely unsuitable for a robust application like n8n.10 Shared hosting environments force multiple websites to share the same server resources—including CPU, RAM, and storage—leading to unpredictable performance that can be severely impacted by the resource demands of other users. Furthermore, shared hosting often restricts server access and customization, which is a major limitation for a platform that relies on specific software dependencies and requires direct access to its host environment.10
For these reasons, a Virtual Private Server (VPS) is the only viable solution for self-hosting n8n. A VPS carves out a separate, isolated virtual space on a physical server, guaranteeing a dedicated set of resources for each user.10 This ensures that your n8n instance will not compete for resources with other hosted applications, providing a stable, high-performance environment. A VPS offers the control and flexibility of a dedicated server at a fraction of the cost, giving users the ability to install and manage their own software and operating systems, which is a fundamental requirement for the n8n ecosystem.10
2.2 Hostinger’s Tailored VPS Plans for Self-Hosting n8n
The technical requirements for self-hosting n8n are specific, recommending a modern multi-core processor (2 cores minimum, 4 recommended), at least 2 GB of RAM (4 GB or more recommended), and a minimum of 20 GB of SSD storage.11 Hostinger directly addresses these needs with its KVM VPS plans, which are explicitly tailored and advertised for self-hosting n8n.12 These plans come with a one-click installation template and are designed to provide the necessary resources for various use cases.12
Selecting the right Hostinger plan depends on the scale and complexity of the automation workflows. For personal projects or light automation needs, a plan with a minimum of 2 vCPU cores and 4 GB of RAM is recommended.7 For small-to-medium businesses or online stores with more complex workflows, a plan with 2 virtual CPU cores, 8 GB of RAM, and 100 GB of NVMe SSD storage, such as the KVM 2 package, is a comfortable choice.12 This tiered plan structure provides a clear growth path, allowing a user to start small and easily upgrade their resources as their automation needs expand.12
| Hostinger VPS Plan | Price (Renews at) | vCPU Cores | RAM | NVMe Disk Space | Bandwidth | Recommended Use Case |
| KVM 1 | US$ 4.99 /mo ($9.99) | 1 | 4 GB | 50 GB | 4 TB | Small-scale personal projects and basic, low-volume automations. |
| KVM 2 | US$ 6.99 /mo ($12.99) | 2 | 8 GB | 100 GB | 8 TB | Small-to-medium businesses, online stores, and high-volume tasks. |
| KVM 4 | US$ 9.99 /mo ($24.99) | 4 | 16 GB | 200 GB | 16 TB | Large-scale projects, data-intensive workflows, and AI pipelines. |
| KVM 8 | US$ 19.99 /mo ($49.99) | 8 | 32 GB | 400 GB | 32 TB | Enterprise-level deployments and mission-critical applications. |
2.3 The Hostinger Advantage: Support, Ease of Use, and Value
The perceived complexity of self-hosting is a significant barrier for many users. Hostinger’s approach to this challenge is to simplify the entire process, making a powerful tool like n8n accessible to a broader audience. While the self-hosted model can sometimes be seen as a “maintenance nightmare,” Hostinger’s user-friendly hPanel, 24/7 customer support, and AI assistant, Kodee, actively work to mitigate these concerns.12 For example, the AI assistant can help with server management and security settings using natural language, providing a level of support that is not typically available with standard VPS providers.12
Beyond the technical support, the value proposition of the Hostinger + n8n combination is compelling. By choosing a Hostinger VPS plan, a user gains access to a full-featured n8n Community Edition without any usage limits. This translates to “unlimited workflows” and “unlimited concurrent executions” for a single, predictable monthly fee.12 This direct contrast to the task-based pricing of competitors makes the solution uniquely appealing for a business focused on scaling without incurring unpredictable costs.12 Hostinger’s product engineering has strategically addressed the complexity and cost friction points of self-hosting, transforming itself from a generic server provider into a value-added partner in the automation ecosystem. The result is a uniquely powerful and accessible solution that empowers users to take full control of their data and infrastructure.
Part II: Comprehensive Step-by-Step Deployment Guide
Chapter 3: Getting Started with Hostinger
3.1 Account Setup and VPS Selection
The initial step is to select a Hostinger KVM VPS plan from the range of options available. Once a plan is chosen, the user must complete the account setup and payment process. The Hostinger hPanel dashboard will serve as the central control hub for all subsequent steps.
3.2 Accessing Your Server via SSH: A Primer on Secure Connection
Secure Shell (SSH) is a cryptographic network protocol that provides a secure way to access and manage a remote server. For Hostinger’s Web Premium and Cloud hosting plans, SSH access is restricted to the user’s home directory and below. The first step to using SSH is to enable it directly from the Hostinger hPanel. Within the Websites dashboard, an option for “SSH Access” can be found on the sidebar. Clicking “Enable” will activate the feature, allowing an SSH connection to be established.15
For enhanced security and ease of use, it is highly recommended to use a public and private key pair for SSH authentication instead of a password.16 The private key is stored on the user’s local machine, while the public key is stored on the remote server. When a connection is attempted, the server uses the public key to verify the identity of the user based on their private key, creating a secure and encrypted channel.16 Hostinger supports both the older RSA algorithm and the more modern Ed25519 algorithm.16 The key generation process can be initiated using the
ssh-keygen command in a terminal. After generating the key pair, the user must log into the hPanel, navigate to the VPS menu, and add the public key (.pub file) in the “SSH keys” settings. The private key should never be shared with anyone.16 This straightforward process, integrated into the Hostinger dashboard, streamlines a traditionally complex task, making the self-hosting journey less intimidating for the technical enthusiast.
Chapter 4: Deployment Method 1: The One-Click Template
This method is the most straightforward, efficient, and safest way to self-host n8n, especially for beginners.7 By using a preconfigured OS template, the system automatically handles the installation and configuration of n8n and its dependencies, helping to avoid errors that can arise from manual command execution.7
- Log in to hPanel: Access your Hostinger account using your preferred method.
- Navigate to VPS Management: Once logged in, go to the “VPS” section from the left-hand menu.
- Select Your VPS: Choose the specific VPS you want to install n8n on and click the “Manage” button next to it.
- Change the Operating System: In the VPS dashboard, locate the “OS & Panel” dropdown menu on the left and select “Operating System.”
- Choose the n8n Template: From the list of available templates, select “Ubuntu 24.04 with n8n.”
- Initiate Installation: Confirm your choice, and the Hostinger system will begin the process of automatically installing and configuring n8n.7
- Access the Application: Once the installation is complete, you can access your n8n instance by returning to the VPS Overview page and clicking “Manage App”.7
Chapter 5: Deployment Method 2: The Advanced Docker Approach
For technical users who desire greater control, isolation, and simplified management, running n8n in a Docker container is the recommended method.7 This approach is more reliable than a manual npm installation, as it isolates n8n from the main system and simplifies the management of its dependencies and future updates.7
5.1 Prerequisites: Installing Docker and Docker Compose
To begin, the user must ensure that Docker and Docker Compose are installed on the VPS. Hostinger offers a pre-configured Docker VPS hosting plan that makes this a one-step process.17 For other plans, Docker can be installed manually via the command line.
5.2 Creating the Docker Compose File and Configuring Environment Variables
A docker-compose.yml file is used to define and run the n8n container. This file specifies the container image, the necessary ports to expose, and the persistent data volumes to ensure that workflow data and credentials are not lost if the container is restarted.17
Below is an example of a simple docker-compose.yml file. It is essential to replace yourUser and yourPassword with secure credentials to enable basic authentication from the start.3
YAML
version: '3.8'
services:
n8n:
image: n8nio/n8n
container_name: n8n
restart: always
ports:
- "5678:5678"
volumes:
- n8n_data:/home/node/.n8n
environment:
- N8N_BASIC_AUTH_ACTIVE=true
- N8N_BASIC_AUTH_USER=yourUser
- N8N_BASIC_AUTH_PASSWORD=yourPassword
- N8N_ENCRYPTION_KEY=your_encryption_key_here
- N8N_PORT=5678
volumes:
n8n_data:
5.3 Launching and Securing the n8n Container
With the Docker Compose file configured, the n8n container can be launched with a single command: docker compose up -d.17 The container will be started in the background, and the n8n instance will be accessible through the VPS’s IP address on port 5678.
For a production environment, securing the connection with HTTPS is mandatory, as n8n requires a secure cookie by default.7 This is crucial for authentication and for nodes that rely on secure APIs.14 The standard method involves using an NGINX web server as a reverse proxy and Certbot to automatically issue and manage a free SSL certificate from Let’s Encrypt.11 An alternative, simpler method is to use a Cloudflare Tunnel, which can expose the instance securely over HTTPS without the need for manual reverse proxy or SSL certificate management.14
Part III: Mastering Your Self-Hosted Environment
Chapter 6: Essential Post-Installation Security and Configuration
6.1 Securing Your Instance with Basic Authentication and HTTPS
After deployment, the first and most critical step is to secure the n8n instance. This prevents unauthorized access to the visual builder and to the sensitive credentials and data stored within the platform. Basic authentication can be enabled by setting the N8N_BASIC_AUTH_USER and N8N_BASIC_AUTH_PASSWORD environment variables.3 It is imperative to use a strong, unique password for these credentials and to consider using a password manager to generate and store them securely.11 For an additional layer of protection, n8n also supports Two-Factor Authentication (2FA) which can be enabled in the user settings after logging in.11
As previously noted, an SSL certificate is required to enable HTTPS. This is not merely a security best practice; it is a requirement for n8n’s secure cookie policy and for many API-based nodes that mandate a secure connection.7
6.2 Configuring Webhook URLs and Resolving Common Connection Issues
One of the most common issues encountered during self-hosting is a failure of webhooks to function correctly. By default, n8n may generate webhook URLs using http://localhost:5678/webhook/..., which is unusable for external services that need to connect to the instance.14 The solution is to explicitly set the public URL of the n8n instance by configuring the
WEBHOOK_URL environment variable. For example, setting WEBHOOK_URL=https://yourdomain.com ensures that all generated webhook URLs are correct and accessible to external services.14 Furthermore, it is important to check firewall settings, as some may block the default port 5678, preventing external access to the webhook.14
6.3 Ensuring Data Persistence with PostgreSQL
By default, n8n uses a simple SQLite database to store workflow data, which is saved to the local disk. While this works for basic testing, it is not recommended for production environments where reliability and scalability are paramount.11 For a more robust and scalable setup, it is a best practice to use an external database like PostgreSQL.11
The process involves installing PostgreSQL on the VPS, creating a dedicated database and user for n8n, and then configuring n8n to use it by setting the necessary environment variables in the .env file or Docker Compose file.11 These variables include
DB_TYPE=postgresdb, DB_POSTGRESDB_HOST, DB_POSTGRESDB_DATABASE, DB_POSTGRESDB_USER, and DB_POSTGRESDB_PASSWORD.11 This ensures that all workflow execution data, logs, and other critical information are stored in a persistent, scalable, and reliable manner.13
Chapter 7: Scaling and Advanced Architecture
7.1 When to Upgrade: Vertical Scaling Your VPS
As automation workflows grow in complexity and volume, the single-instance n8n setup may eventually experience performance bottlenecks. The simplest and most immediate solution to this challenge is vertical scaling. This involves increasing the resources of the current VPS, such as upgrading the CPU, RAM, and storage.11 Hostinger’s VPS plans are designed for easy upgrades, allowing a user to transition to a more powerful plan with a few clicks via the hPanel.12 This strategy works well for small to medium-sized deployments and provides the necessary headroom for future growth.13
7.2 The n8n Queue Mode: A Deep Dive into Horizontal Scaling
For businesses that require high-volume, mission-critical automation, vertical scaling has its limits. The next logical step is to adopt a horizontal scaling strategy by implementing n8n’s Queue Mode.13 This advanced architecture fundamentally separates the n8n instance into distinct, decoupled components, a design pattern used in modern, scalable enterprise applications. The core of this architecture is a job queue that distributes tasks across multiple dedicated worker processes, preventing a single process from becoming a bottleneck.13
This decoupled architecture consists of three key components:
- The Main n8n Instance: This component is responsible for the visual interface, workflow configuration, and handling all triggers.13 It serves as the user-facing application but does not execute the workflows itself.
- Redis: This key-value database acts as a message broker and is a critical component for the job queue.13 When a workflow is triggered, the main instance places a job in Redis’s queue.
- Worker Processes: These are separate n8n instances that are launched in “worker mode.” Their sole responsibility is to continuously pull pending jobs from the Redis queue and execute the automation steps in parallel.13
This decoupled architecture ensures that even with a high volume of concurrent workflow executions, the n8n system remains performant and reliable. It confirms that the self-hosted n8n solution is not just a hobbyist tool but a robust, production-grade platform capable of handling enterprise-level workloads.
Diagram 1: n8n Queue Mode Architecture
The following diagram provides a visual representation of the decoupled architecture for horizontal scaling using n8n Queue Mode.
+------------------+ +-----------------+ +----------------------+
| Main n8n Instance|-----| Message Broker |<----| Worker Process (1) |
| (UI & Triggers) | Job| (Redis) | | (Execution) |
+------------------+---->| Queue | +----------------------+
| hPanel | +-----------------+ +----------------------+
| (User) | | Worker Process (2) |
| ... | | (Execution) |
+------------------+ +----------------------+
^
|
v
+------------------+
| PostgreSQL DB |
| (Data Storage) |
+------------------+
Chapter 8: Practical Workflow Examples for Hostinger Users
This section provides concrete examples of how n8n can be used to solve real-world business problems, showcasing the power and flexibility of the platform.
8.1 AI-Powered Social Media Management
A business can automate its social media monitoring and reporting using n8n. A workflow can be configured with a scheduled trigger to run daily or weekly, fetching mentions and engagement metrics from various platforms like Facebook, LinkedIn, and Instagram.20 For a deeper level of analysis, a subsequent node can use an AI model, such as OpenAI or DeepSeek, to perform sentiment analysis on the mentions, classifying them as positive, neutral, or negative.20 The data can then be organized using a
Set node and sent as an automated report via email or a summary to a Slack channel for a team to review.20 This workflow automates not just the data collection, but also the interpretation of that data, providing valuable, actionable insights without manual effort.
8.2 E-commerce Data Synchronization and Reporting
For an e-commerce business, n8n can automate the entire order fulfillment and reporting process. A workflow can be initiated by a webhook triggered by a new order. The first step would involve using a Check or If node to validate the customer’s existence in a database, preventing duplicate entries.20 The workflow can then proceed to verify payment status and check for fraud using external services.2 Upon successful validation, the workflow can automatically generate an invoice, using a node to convert data into a PDF, and email it to the customer.2 All of this data can be stored in a central database or Google Sheets, from which a separate scheduled workflow can pull and compile weekly reports, adding them to a meeting notification.2
8.3 Automating Business Processes with Document Analysis
n8n excels at streamlining internal business processes, such as document analysis and routing. A workflow can be configured to trigger on a new document upload. A Switch node can be used to handle different file types, routing each to a specific process.20 An “Extract from File” node can then pull relevant data from the document. For an added layer of intelligence, an advanced AI node can be used to generate a summary of the document, which can then be sent to a manager for review via email or a messaging platform like Slack.20 If the document is approved, the workflow can store the decision in a database and move the document to the next stage of the process.
Chapter 9: Troubleshooting and Maintenance
9.1 Common Issues and Solutions
Despite the streamlined installation process, self-hosting can present unique challenges. A common problem is the failure of webhooks, which can be caused by the webhook URL defaulting to localhost or by firewall settings blocking port 5678.14 The solution involves ensuring the
WEBHOOK_URL environment variable is set to the correct public URL and testing the connection to the webhook from an external system. Nodes failing to connect to APIs is often due to the lack of HTTPS on the self-hosted instance, a problem that can be solved by properly configuring a reverse proxy or using a Cloudflare Tunnel.14
9.2 Best Practices for Updates, Backups, and Security Audits
For a reliable and secure self-hosted n8n environment, continuous maintenance is essential. It is a best practice to keep the n8n instance updated to the latest version to access new features and security patches.7 Users should also ensure that their data is persistent by using a dedicated database like PostgreSQL and that a regular backup schedule is in place to prevent data loss in the event of an issue.7 Regular security audits and ensuring all authentication protocols are active are also critical for protecting sensitive data and credentials stored within the platform.
| Configuration Item | Environment Variable | Recommended Value/Solution | Importance |
| Basic Authentication | N8N_BASIC_AUTH_USER, N8N_BASIC_AUTH_PASSWORD | Strong, unique credentials | Prevents unauthorized access to the n8n instance and its data. |
| Webhook URL | WEBHOOK_URL | Your public domain or IP address with HTTPS | Ensures webhooks are externally accessible and functional. |
| Database | DB_TYPE, DB_POSTGRESDB_HOST, etc. | PostgreSQL (recommended) | Provides a persistent, robust, and scalable data store for production. |
| SSL/HTTPS | Handled via NGINX/Certbot or Cloudflare Tunnel | HTTPS enabled | Required for secure cookie policy and many API integrations. |
| Encryption Key | N8N_ENCRYPTION_KEY | A long, random string | Encrypts sensitive data in the database for security. |
| Queue Mode (Advanced) | N8N_QUEUE_ACTIVE, N8N_QUEUE_REDIS_URL, etc. | Decoupled architecture with Redis | Enables horizontal scaling for high-volume workloads. |
Chapter 10: Final Thoughts
This guide has explored the compelling case for self-hosting n8n on a Hostinger VPS, demonstrating that this combination is a powerful and strategic choice for businesses and technical users alike. The analysis has shown that by selecting a solution that is free to self-host, an organization can fundamentally change the economics of its automation strategy. Instead of being constrained by a model that imposes a financial penalty for every task, a business can build the most complex, high-volume workflows without incurring additional costs beyond the fixed price of its server infrastructure. This cost predictability and scalability are invaluable for long-term growth.
Furthermore, the combination of n8n’s open-source flexibility and Hostinger’s user-friendly tools directly addresses the primary friction points of self-hosting. Hostinger’s preconfigured one-click template and dedicated VPS plans for n8n demystify the initial setup, while its ongoing support and AI-powered management tools mitigate the concerns of long-term maintenance. The result is a solution that empowers a user to take full control of their data and infrastructure, build infinitely customizable workflows, and scale their automation with confidence. This self-hosted model is not merely a viable alternative to cloud-based solutions; for any business that prioritizes data ownership, cost control, and a clear path to scalability, it is a superior, future-proof choice.
More News
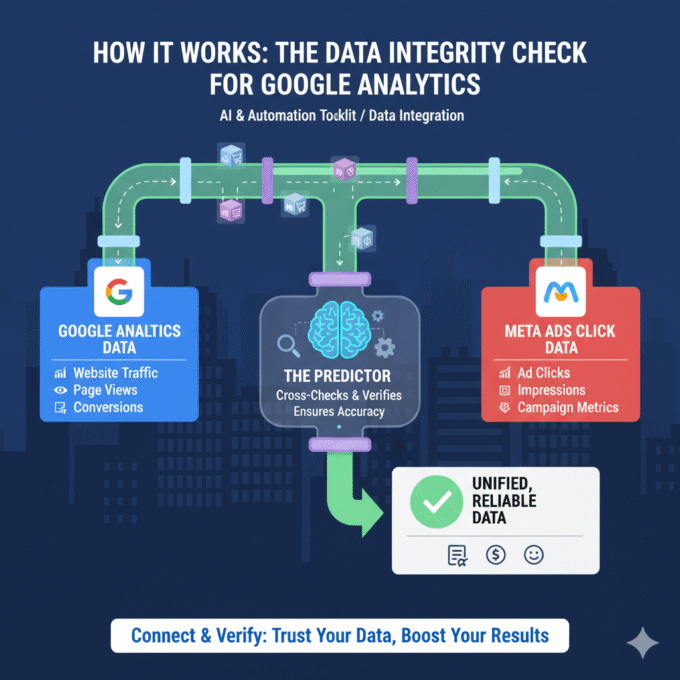
The Data Integrity Check for Google Analytics
How It Works: The Data Integrity Check for Google Analytics In the...
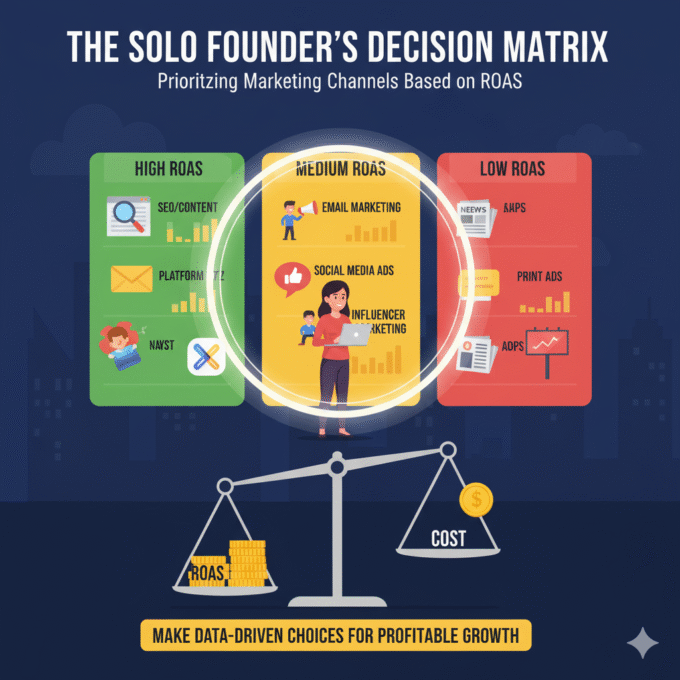
October 21, 2025The Solo Founder’s Decision Matrix: Prioritizing Marketing Channels Based on ROAS
The Solo Founder’s Decision Matrix As a solo founder, your most precious...
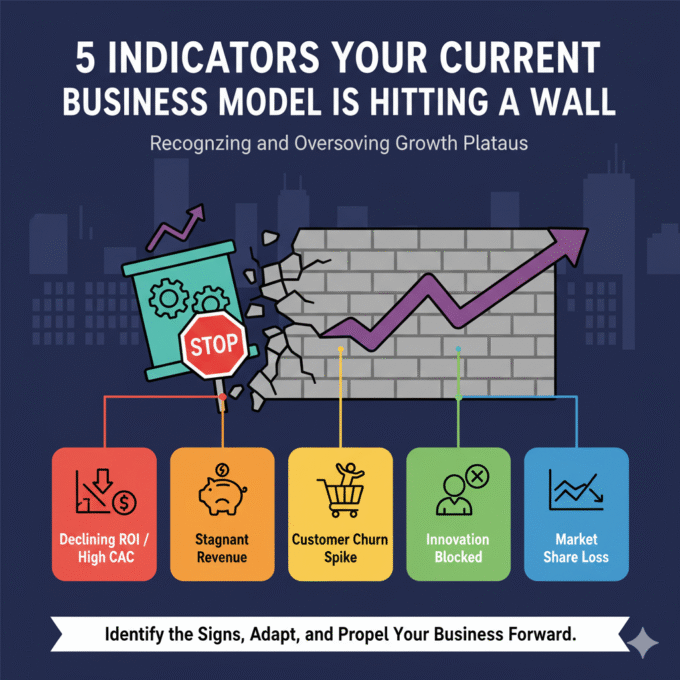
October 21, 20255 Indicators Your Current Business Model is Hitting a Wall
5 Indicators Your Current Business Model is Hitting a Wall The success...
October 21, 2025The Automated Lead Engine: Steps to Automate Lead Generation with Meta Lead Ads
Steps to Automate Lead Generation with Meta Lead Ads Meta Lead Ads...
October 20, 2025META Andromeda update main secret
Creative as a Data Signal: How Meta’s Andromeda Update Rewrote the Rules...
October 20, 2025Meta Andromeda: The Next-Generation AI Engine for Performance Growth
I. Executive Summary: The Andromeda Paradigm Shift 1.1. Introduction to the AI...
October 14, 2025The Data Integrity Check for Google Analytics
How It Works: The Data Integrity Check for Google Analytics In the...
October 21, 2025The Solo Founder’s Decision Matrix: Prioritizing Marketing Channels Based on ROAS
The Solo Founder’s Decision Matrix As a solo founder, your most precious...
October 21, 20255 Indicators Your Current Business Model is Hitting a Wall
5 Indicators Your Current Business Model is Hitting a Wall The success...
October 21, 2025The Automated Lead Engine: Steps to Automate Lead Generation with Meta Lead Ads
Steps to Automate Lead Generation with Meta Lead Ads Meta Lead Ads...
October 20, 2025